Czech Point Research security researchers note increasing hacking activity by malware Zloader
[datensicherheit.de, 05.01.2022] “Zloader”, a Bank Trojan, Check Point® Software Technologies Ltd. According to the latest findings of CheckPoint Research (CPR) security experts in the field of “Back in advance” – So they suspect they are hackers Place the “Molsmok” board behind it.
Image: CPR
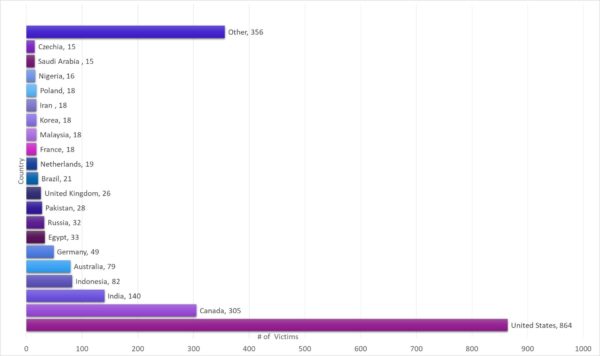
Current hacking campaign It has targeted more than 2,100 victims in 111 countries
Malsmock hacking group misuses Google keyword ads to spread malware
Security researchers need “Malware ‘Zloader’ Activity Increases” Observed. What is special about it is that this malicious software is used Microsoft file signatures To give a legitimate look. However, the digital watermark has changed.
In the summer of 2021, “ZLoader” was particularly noticeable during the summer months, when the “MalSmoke” team, the operators of this malware, acquired some of Google’s top advertisements to spread various malware strains, including the infamous one. “Ryuk” – Ransomware.
“In the course of the current campaign, Checkpoint security experts have so far been able to identify more than 2,100 victims in 111 countries. Germany is in sixth place. “
Hackers continue to create malware campaigns to make effective countermeasures more difficult
Infectious chain lt. CPR:
- The attack begins with the establishment of a proper remote management plan, “It pretends to be a ‘Java’ installation”.
- After this installation, the attacker gains full access to the system and is able to upload, download, and execute scripts. “The attacker uploads some scripts and executes them.” These will download more scripts that will run “mshta.exe” as a parameter in the “appContast.dll” file.
- The “appContast.dll” file actually looks like it was signed by Microsoft, “Even if additional information is added at the end of the file”.
- Added info Download the final “ZLoader” payload and run it, “Stealing Victims’ Credentials and Personal Information”.
In addition, those responsible further developed this malware campaign weekly To make the effective resistance much harder.
Based on the analysis of the current campaign method, those behind it, compared to previous malware attacks Responsible for “Malsmock” Play.
The first evidence of a new hacker campaign discovered in November 2021
“People need to know that they are Do not immediately trust the digital signature of a file Can. We’ve detected a new ‘ZLoader’ campaign that uses Microsoft’s digital signature verification to steal sensitive information from users. “, Kobe Eisencraft, Czech point malware researcher, warns in his report. The first signs of this new campaign were discovered in November 2021.
Eisencraft does: The attackers, whom we call ‘Molsmok’, stole it User testimonials and personal information of the victims Except. So far more than 2,000 people have been affected in 111 countries, and the number is growing. Overall, Zloader campaign operators seem to be putting a lot of effort into avoiding security and updating their systems on a weekly basis.
Eisencraft strongly recommends that users “Install Microsoft Update for strict authentication code verification as it will not be used by default”. As part of its responsibility, Checkpoint already owned Microsoft and Adora immediately The results of the investigation were reported.
Additional information on the topic:
cp
Can you trust the digital signature of a file? The new Zloader campaign is using Microsoft’s signature verification to put users at risk

Professional bacon fanatic. Explorer. Avid pop culture expert. Introvert. Amateur web evangelist.










More Stories
What Does the Future of Gaming Look Like?
Throne and Liberty – First Impression Overview
Ethereum Use Cases