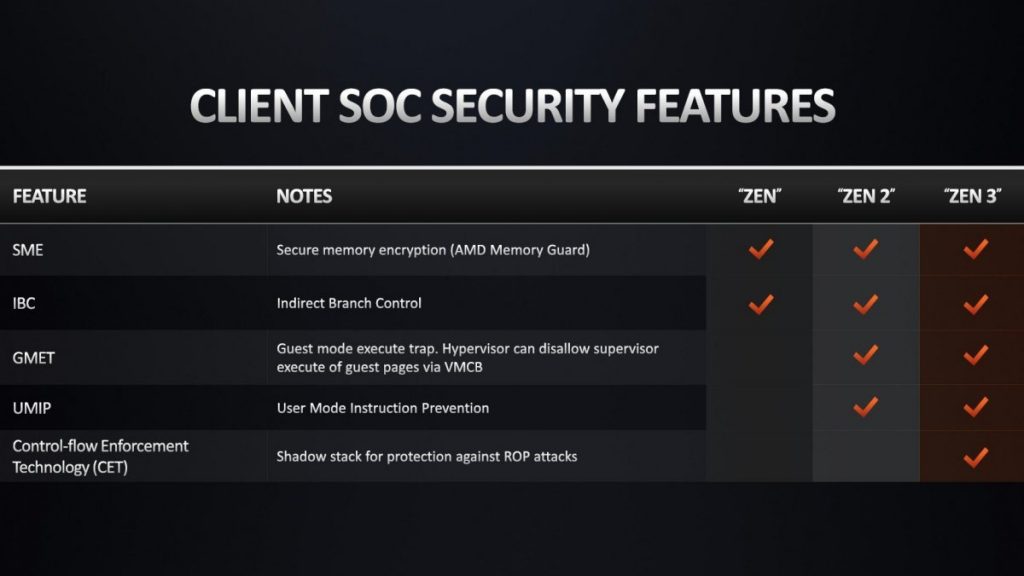
To avoid security measures, some malicious programs rely on Return Oriented Programming (ROP) or Jump Oriented Programming (JOP). Some modern processors, such as the Raison 5000U’s AMD mobile processors and the 5000h series with Gen-3 technology, are said to make such attacks much harder by the “shadow layer”.
In 2016, Intel released the Control-Flow Enforcement Technology (CET) as a ROP / JOP alternative that can only be used on the latest Core-I processors of the eleventh generation “Tiger Lake”. AMD also uses the word CET in the current one AMD64 Architectural Programmer’s Guide to Volume 2: Computer Programming (PDF file)Explains implementation. Apparently, the AMD CED has so far only been built into systems-on-chip (SoCs) with the Gen3, not the AM4 versions of the Risen 5000.
Microsoft wants to use the CED functionality of x86 processors with a future update of Windows 10, but so far only the preview version of Windows 10 has shadow layer (SHSTK) support. To the Linux kernel Intel has developed a CED patch. Apple generates an ARM number called the CED Pointer Authorization Code (PAC) A12 first on the company’s own processors.
The ARM CPU cores themselves are PAC capable from the upcoming Cortex-A78C, which is also targeted at Windows notebooks. Future processors should have additional functions that make attacks more difficult, including memory tagging.

(Order)

“Avid writer. Subtly charming alcohol fanatic. Total twitter junkie. Coffee enthusiast. Proud gamer. Web aficionado. Music advocate. Zombie lover. Reader.”











More Stories
Acrylic Nails for the Modern Professional: Balancing Style and Practicality
The Majestic Journey of the African Spurred Tortoise: A Guide to Care and Habitat
Choosing Between a Russian and a Greek Tortoise: What You Need to Know