Microsoft targets Azure developers with “large-scale” attacks by malicious npm packages.
On Wednesday, cybersecurity researchers at JFrog reported it Hundreds of malicious packages Created and identified to steal personal data from developers.
According to researchers Andrey Polkovnychenko and Shachar Menashe, the repositories were first discovered on March 21 and grew to more than 200 out of 50 malicious npm pockets in a few days.
Administrators of npm repositories have created automated scripts in npm that target @azure modules, as well as @ azure-rest, @ azure-tests, @ azure-tools and @ cadl-lang.
The script is responsible for creating accounts and uploading npm data, including container services, the Healthbot, testers, and storage packages.
JFrog claims that typosquoting was used to trick developers into downloading malicious files. At the time of writing, these packages contain information-stealing malware.
Typosquatting is a form of phishing that involves making small changes to an email address, file, or web address to impersonate a formal service or content. For example, the attacker “your-cOhBy registering a domain name with “your-c0mpany.com” mpany.com “The attacker hopes that victims will not notice that the source is fraudulent by replacing this single character with another character similar in appearance.
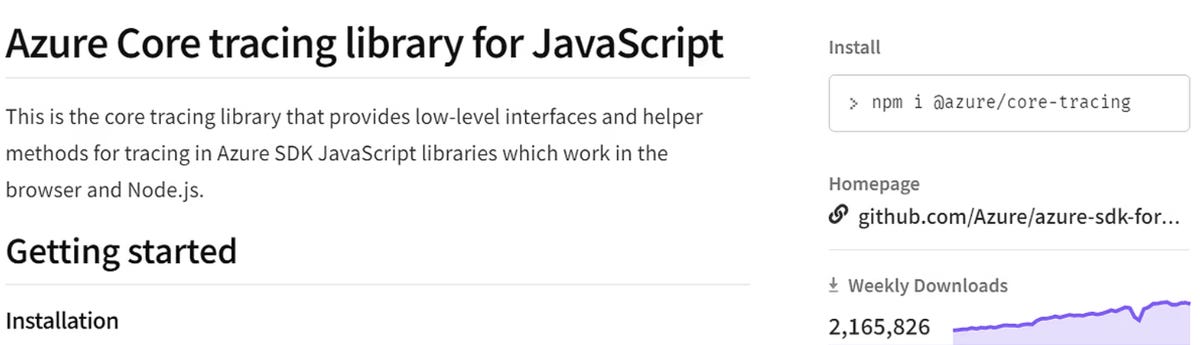
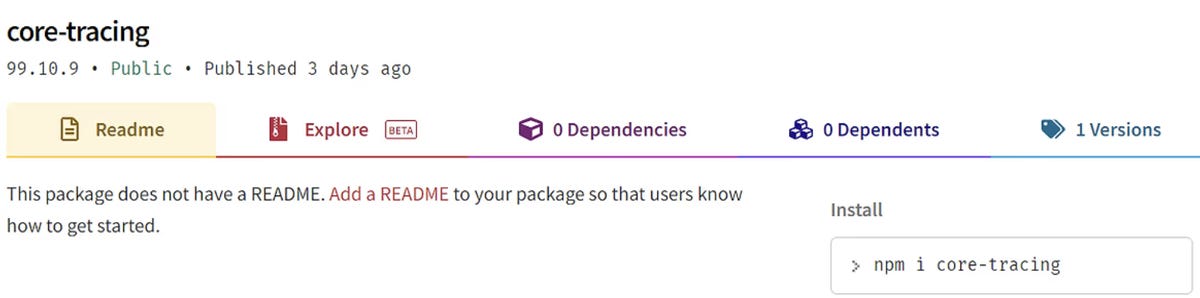
In this case, malicious packages with the same name as the existing @azure scope package are created, but they have abandoned the scope.
Legitimate version
Malicious version
J Frog
“Attacker relies on the fact that some developers may incorrectly avoid the prefix @azure when installing a package,” the researchers explain. “For example, npm install core-tracing by mistake – instead of the npm install @ azure / core-tracing command”.
Also, all npm packages received high version numbers, which may indicate pro-confusing attacks.
“Since this set of legitimate packages is downloaded millions of times each week, there is a good chance that some developers will be successfully deceived by the typosquat attack,” JFrog adds.
Presented by JFrog A complete list Malicious npm packages have been detected so far. Npm maintainers have removed malicious files, but Azure developers need to be vigilant for further functionality of this cast.
Source: “ZDNet.com”

Professional bacon fanatic. Explorer. Avid pop culture expert. Introvert. Amateur web evangelist.











More Stories
Acrylic Nails for the Modern Professional: Balancing Style and Practicality
The Majestic Journey of the African Spurred Tortoise: A Guide to Care and Habitat
Choosing Between a Russian and a Greek Tortoise: What You Need to Know