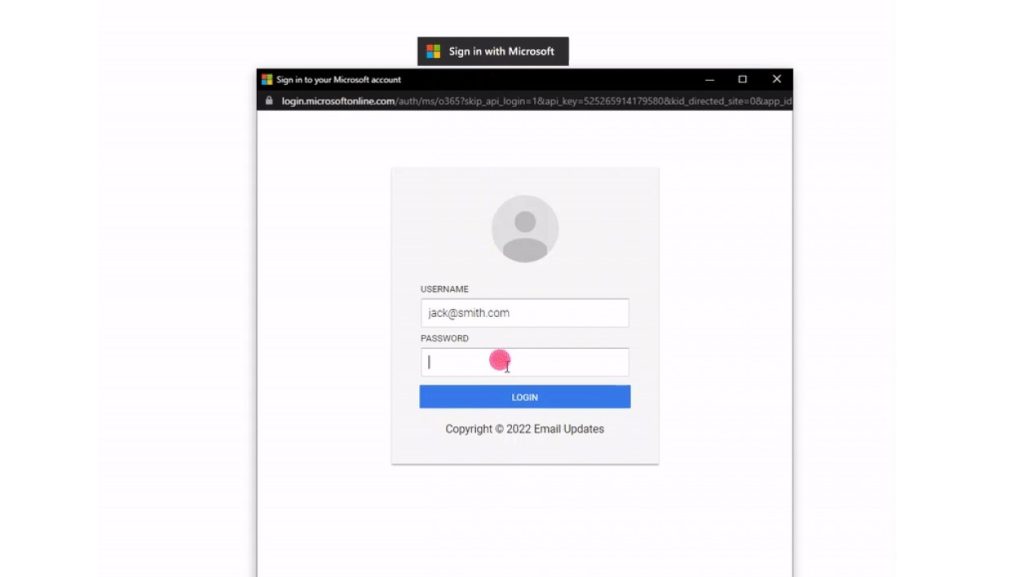
Beware of fake login pop-ups! Security Analyst “mr.d0x” has shown that it is possible to follow these access restrictions so that they are not visually identifiable from originals made by Facebook and Microsoft. Most worryingly, the techniques used are not complicated because they rely solely on HTML / JavaScript language and CSS stylesheets.
By combining everything wisely, you will get the perfect login window suitable for phishing. Even the URL seems perfectly legitimate … when in fact it is a simple text bar. Small Patlock – should show a secure TLS connection – is nothing more than a GIF image. A real craft, the Facebook link below proves Moka.

Checking the start button or link on this window will not detect the pot of roses. Thanks to JavaScript, you can fill in the URL that is displayed when the cursor moves over it, but if you click on it you can run another one. Clever!
However, there is a way to realize this fraud. Launching this fake login window can only be done from a fake website, which will display a suspicious URL. But it still needs to be realized. For example, the hacker has posted link samples and a short presentation video on GitHub. Now you have been warned.
Proof : mr.d0x (Via Hacker News)

“Avid writer. Subtly charming alcohol fanatic. Total twitter junkie. Coffee enthusiast. Proud gamer. Web aficionado. Music advocate. Zombie lover. Reader.”










More Stories
Acrylic Nails for the Modern Professional: Balancing Style and Practicality
The Majestic Journey of the African Spurred Tortoise: A Guide to Care and Habitat
Choosing Between a Russian and a Greek Tortoise: What You Need to Know