Microsoft warns about the current malware campaign, during which emails are mainly sent to companies using contact forms. Under one false pretense, recipients should be prompted to click on the link in the emails in order to eventually capture the bank Trojan “ICIDIT”.
It is questionable whether the masterminds behind the current campaign are specifically targeting German users. Access to Microsoft Security Blog Not revealed. High Security has asked Microsoft about this, but has not yet received an answer. However, ICIDIT is not new to this country: in the past, the modular Trojan was reloaded by Emotet with others, and security experts have already warned about the malware several times this year. So caution is needed in any case.
Double ambiguity
The campaign described by Microsoft is targeting business operators with Gmail-based web sites – known or publicly available to the attacker from data leaks, for example as an alternative contact option – i.e. Google Account. If this requirement is met, attackers can use the double blur technique.
First, they mislead the recipient and spam filtering methods by using the contact form alternate route as a reliable sender. In their respective emails, they place a link to Google Sites, a web hosting service (https://sites.google.com/ (…)), You have previously stored malicious code (or redirect to malicious code). You are configuring Google sites so that the code can only be accessed by entering the victim’s Google access data (or access data from an authorized Google group). According to Microsoft, this additional layer of authentication contributes to the fact that it’s difficult to identify email harm by authentication methods.

Google sites can be configured as public, but alternatively access to selected Gmail addresses or Google Groups.
(Image: Screenshot)
The stored malicious code is in a ZIP archive, and it is back in disguise; Only at the end when this code is executed IcedID Reloaded. In addition, according to Microsoft, a (really legitimate) infiltration test tool, Cobalt Strike (Beacon), will be installed so that attackers can remotely control compromised systems and spread further over the network. Once infected, they can eject banking and other data, among other things, but also reload the malware.
Automatically sent charges for stolen images
The emails that Microsoft noticed included allegations of unauthorized use of the respective website and allegations that the document contained evidence in a file with Google sites. To increase the pressure on the victims, there are also threats of legal consequences if the questionable images are not removed. Microsoft cites several senders ending in .yahoo.com and aol.com (mphotographer550, mephotographer890, mgallery487, mephoto224, megallery736 and mshot373) as examples of email addresses entered in the contact form.
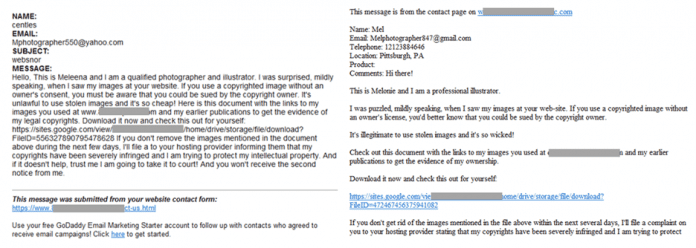
Microsoft has released sample emails from the malware campaign.
(Image: Microsoft)
Considering the larger purpose of the campaign, Microsoft believes that sending mails can be automated using a tool that bypasses Google’s ReCAPTCHA mechanism. How this happens is not clear from the blog post; We also asked Microsoft about this. Just a few months ago the audio version of ReCAPTCHA, which had already been hacked several times, was again successfully tampered with by a researcher.
According to Microsoft, companies need to keep in mind that in the future, similar campaigns could provide other malicious code instead of ICDIT. The wording and excuses of emails sent using the form will vary greatly in the future.
(ovw)

“Avid writer. Subtly charming alcohol fanatic. Total twitter junkie. Coffee enthusiast. Proud gamer. Web aficionado. Music advocate. Zombie lover. Reader.”











More Stories
Acrylic Nails for the Modern Professional: Balancing Style and Practicality
The Majestic Journey of the African Spurred Tortoise: A Guide to Care and Habitat
Choosing Between a Russian and a Greek Tortoise: What You Need to Know