However, as with other common technologies, the widespread use of QR codes has attracted the attention of fraudsters for criminal purposes. The trend also prompted a warning from the United States Federal Bureau of Investigation (FBI).
How do fraudsters use codes for illegal purposes?
What is a QR code and how does it work?
Abbreviation for “quick response”, QR code is a type of barcode that can be read instantly by a machine. The QR code can be up to 4,296 characters, which allows for easy decoding by the smartphone camera.
Text strings encoded in QR code may contain different data. The action that is triggered by reading the QR code depends on the application that interacts with that code.
You can use the codes to go to the website, download the file, add the connection, connect to the WiFi network and pay.
QR codes are very versatile and can be customized to add logos. Dynamic versions of QR codes allow you to change the content or action at any time. However, this diversity can be a double-edged sword.
How can QR codes be used?
The number of cases of application (and potential for misuse) of QR codes is no exception for fraudsters.
Here’s how cybercriminals can steal codes to steal your data and money:
1. Redirect important information to a malicious website : Phishing attacks are not just spread by emails, instant messages or SMS. Just as they can redirect you to fraudulent sites using malicious ads and other tactics, they can also do this in QR codes.
2. Downloads malicious file to your device : Many bars and restaurants use QR codes to download a menu in PDF format or install an app that allows you to order. To deceive you into downloading malicious PDF file or malicious mobile processor, attackers can easily forge QR code.
3. Trigger actions on your device : QR codes can trigger actions directly on your device, depending on the application that reads these actions. However, there are some basic functions that any QR reader can explain.
This includes connecting the device to a Wi-Fi network, sending an email or text message with pre-defined text, or storing contact information on your device. Although these actions are not malicious, they can be used to connect the device to a compromised network or to send messages on your behalf.
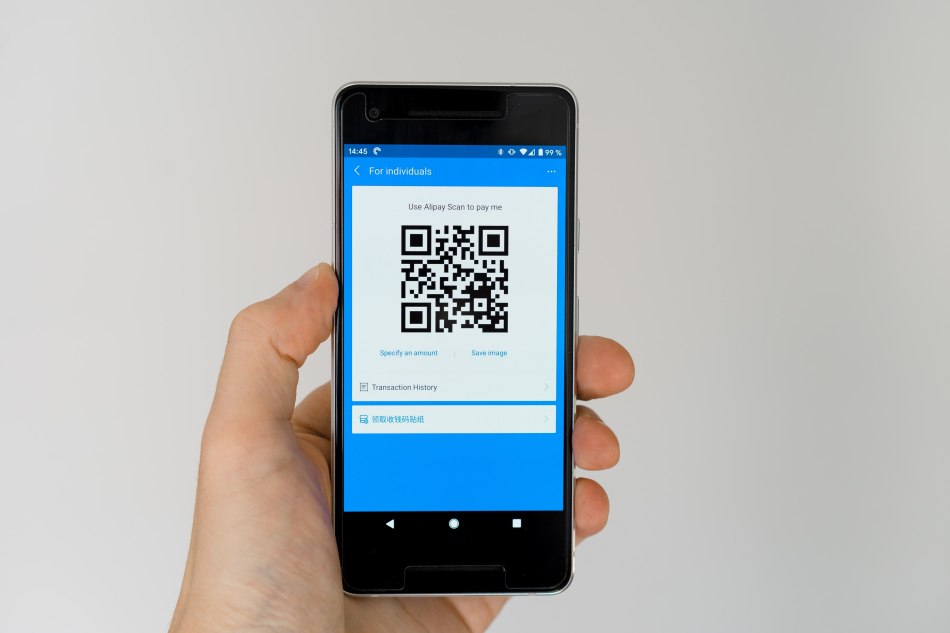
4. Diversify a charge : Most financial applications today allow payments using QR codes containing the recipient’s data. Many stores display these codes to facilitate the transaction.
However, the attacker can change this QR with his own data and withdraw money to his account. You can also create codes with money collection requests to deceive yourself.
5. Steal your identity : Many QR codes are used as certification to verify your information, such as your ID card or vaccination record. In these cases, QR codes may contain sensitive information such as your ID or medical records, which the attacker can easily obtain by scanning the QR code.
We adopted QR codes in our daily lives. And as with all new practices, we need to develop new habits to stay alert. Each new technology brings its share of benefits but also threats.

Professional bacon fanatic. Explorer. Avid pop culture expert. Introvert. Amateur web evangelist.










More Stories
Acrylic Nails for the Modern Professional: Balancing Style and Practicality
The Majestic Journey of the African Spurred Tortoise: A Guide to Care and Habitat
Choosing Between a Russian and a Greek Tortoise: What You Need to Know